Here’s the problem. You go along to http://www.thawte.com and ask to buy a Microsoft authenticode certificate. It’s the right thing to do; signing code is increasingly important in these days of Internet delivery of applications; and unsigned code presents the user with dire warnings that may unnerve them.
So you go to buy a certificate. The way this works is in two stages. When you apply for the certificate, you are issued with a new private key, but not the certificate itself. Thawte then does its due diligence and checks out that you really do represent the organization for which you are requesting a certificate. Finally, you can go back and download the certificate and get on with signing your apps.
This process works differently on Vista than on XP. I got this wrong when I first tried it, because it is not obvious. To begin with, you have to relax IE’s security for the thawte site – ironic, for a security operation – and make sure it is not running in protected mode. Next, the first page of the application is a big form that has the details of the organization, how you are going to pay, and so on. If you complete this on Vista, and click Submit, you get a message saying “This web site is requesting a new certificate on your behalf”:
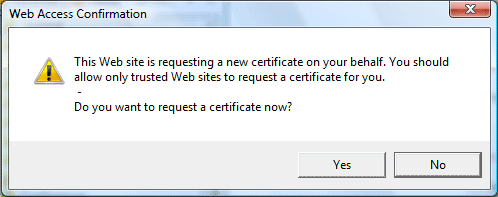
You complete the application, sit back and wait. A few days later you get an email saying your certificate is ready for download. You download it; it is a file called something like mycert.spc. You can right-click and choose Install Certificate, to place it in the Windows certificate store. You can even sign code with it. Just open a Visual Studio command prompt, type:
signtool signwizard
and off you go. You can select the new certificate from your certificate store, timestamp the code (recommended), and you’re done.
So what’s the problem? Well, what if you want to sign code on a different machine than the one on which you applied for the certificate? And what if you want to back up your certificate?
Did you realise when you made the purchase that you were irretrievably hooking the certificate to the actual Vista installation which you were using for the transaction?
It is all to do with the private key. To sign code, you need the private key, which was installed into your certificate store when that first page of the application was submitted. Unfortunately it cannot be exported; it is marked as non-exportable, which means the Export feature of Vista’s Certificate Manager will not allow the private key to be exported. Thawte cannot re-issue the private key; the only solution I know of is to get the entire certificate revoked reissued (fortunately this is a free service).
This problem does not occur on Windows XP. Here is the evidence. The screenshot below shows part of the application form on Vista:
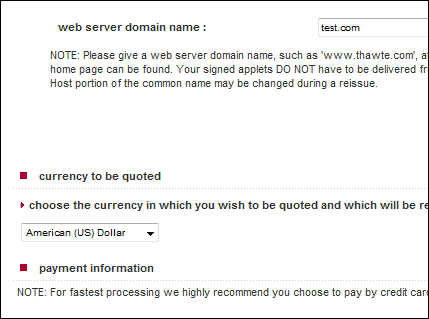
Now, here is the same part of the form on Windows XP (still IE7):
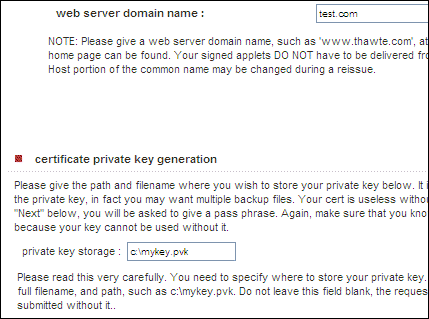
Spot the difference? An additional section appears in XP, which lets you specify where to save your private key as a file with a .pvk extension. On Vista, you don’t get that choice and you don’t get a .pvk file. Once you have both the .pvk and the .spc files, you can backup or move the certificate wherever you want, with full signing capability. You can import the the certificate plus private key into your certificate store using this tool:
http://www.microsoft.com/downloads/details.aspx?FamilyID=F9992C94-B129-46BC-B240-414BDFF679A7&displaylang=EN
which is billed as a tool for Office 2000, but works fine for this purpose.
Now, I guess this is a security feature. If you have these private key files hanging around, they are easier to steal than if they are locked into your certificate store and marked non-exportable. Fair enough, but I’d rather make that decision for myself, than have it imposed by an obscure installation process.