Amazon made multiple cloud announcements yesterday, just ahead of anything Microsoft might be pitching at PDC next week. The Elastic Compute Cloud is out of beta; there’s beta support for Windows 32-bit or 64-bit at $0.125 per hour; there’s a new web-based management console; and new automatic load balancing and scaling.
The last points may be the most significant. Smooth scaling is one of the toughest problems for any enterprise or busy web site. On demand scaling is totally compelling.
There’s still something missing. What if the service goes down? SLAs, sure, but saying to the boss “we’ve got an SLA” is little help if your business is losing thousands every hour through unavailability. I’d like to see something about failover to a non-Amazon service, or some convincing reason why we won’t see repeats of the downtime that has afflicted Amazon a couple of times already this year.
Here’s another sign the service is growing up. WordPress comment moderation shows me some basic info about the source IP of comment posters, and I noticed an item of spam yesterday that was sourced from an Amazon EC2 server:
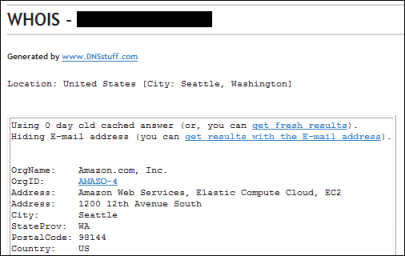
No, it wasn’t one of the new Windows VMs! I traced it to a Swedish site running Plone, emailed the company to point out the problem but haven’t yet had a response. The spam itself makes no sense; probably a test.
Update: I received an explanation from the site:
We have been running a proxy on EC2 that rewrites certain websites for demo purposes. It has just been up for a few days, but it seems that someone thought it was a nice way to relay spam (we only proxy port 80, so just the message board kind).