A couple of days ago I posted about programmatically detecting whether UAC is enabled. I was proposing to read a registry entry. Thanks to the power of blogs, my post drew a comment from Andrei Belogortseff, who has posted C++ code that does this properly. His library has functions for detecting whether the current process is elevated, detecting whether UAC is enabled, and running new processes both elevated and non-elevated (the last of these is the hardest to do).
I liked the libary but wanted to use it from .NET. I compiled his code to a DLL and did a C# wrapper; then I considered the hassles of adding a dependency on the Visual C++ runtime libraries. I therefore did a quick C# implementation of the functions I cared about; I haven’t included the code for running new processes. Please go ahead and download the code, and let me know if you have any suggestions, or even if there is a much easier way to do this that I have missed. There is an app called UACElevationCheck, which calls functions in VistaTools.cs.
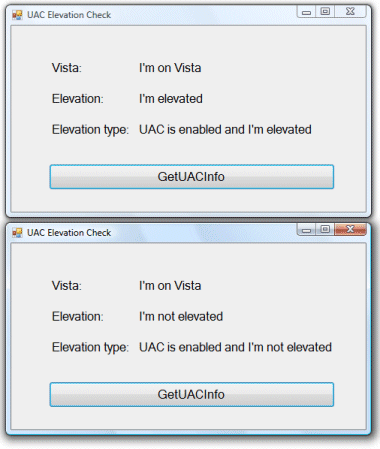
The code is only intended to be called from Vista and will throw an exception otherwise; of course you can modify it as you like.
I’ve included a function IsReallyVista that looks for a Vista-only API call, rather than relying on the reported version information. This is because the version information is unreliable if the app runs in a compatibility mode. On the other hand, IsReallyVista is a hack; if you don’t like it, use IsVista which uses the version information instead.
You may be able to do this using the System.Security namespace rather than PInvoke. I had a quick look but the PInvoke code seemed easier to me, especially since Belogortseff has already done the real work.
Great work!
But the question is how to setup the elevated level, Shouldn’t Vista remember the elevation for a particular app, something like “elevate always!”
You can set this for a shortcut – under Compatibiity – Privilege level.
Tim
Hi,
are you shure your function IsElevated is working correctly? I implemented the same function in Delphi 5 and “GetTokenInformation” always returned 0 running the prog as a not elevated administrator. Your c# implementation is doing exactly the same. I found this: http://groups.google.de/group/microsoft.public.dotnet.framework.interop/browse_thread/thread/63dadce5548b5bfe/931c034b5c7ee48b?lnk=st&q=+TokenElevationType+return+value&rnum=1#931c034b5c7ee48b and changed my Delphi code. Now my code returns TokenElevationTypeLimited for the case mentioned above. Starting my app as an Administartor I’m getting TokenElevationTypeFull. This seems to be correct. I think your function seems to work correctly because you are doing this:
return (te.TokenIsElevated != 0);
cheers
Thomas
Thomas,
The code you reference is passing TokenElevationType as the value of TOKEN_INFORMATION_CLASS, whereas my IsElevated function is passing TokenElevation, which is meant to give a boolean result AIUI. I’ve also implemented GetElevationType which gets the Default/Full/Limited result.
Tim
Hey, I’m really interested in elevating my app from c#. Would it be too much of a hassle to publish that code, the c# wrapper and the dll?
Thanks
Is there a way to elevate the process. I m always getting the second screenshot mentioned above that UAC is enabled but its not elevated.
@Kalyana
See here for how to start a process elevated:
http://www.danielmoth.com/Blog/2006/12/launch-elevated-and-modal-too.html
Thank you for sharing the code. Good work.
btw: You could use Resharper to clean up the code 😉
René
hi can u guys tell me how to use this to stop or start a windows service 🙁 …. PLS HELP ME 🙁
Rajkumar: Starting and stopping windows services can be done through a ServiceController (see sample code). If you don’t have enough rights to access ServiceController, then you will want to run (or perhaps just restart!) your process elevated. That part is described here.
Just an interesting note: The VistaTools class you provide is almost verbatim the exact same that Intuit provides for their QB SDK examples/tools.