Several well-known web sites including The Register, The Daily Telegraph, UPS.comn and Acer.com suffered a DNS hack on Sunday evening. The consequence is that visitors to the sites may see a Turkish hack message.
The hacked sites share a common registrar, Ascio Technologies, and were registered through NetNames. Both NetNames and Ascio are brands of GroupNBT. Zone-h suggests:
It appears that the turkish attackers managed to hack into the DNS panel of NetNames using a SQL injection and modify the configuration of arbitrary sites, to use their own DNS.
This kind of attack is more serious than simply hacking into a web server and defacing the content. DNS maps internet names to the IP numbers that identify actual servers on the internet. This means that the hackers can intercept not only web requests for the affected names, but also email. Hackers could also read cookies placed on user’s computers by the real sites, possibly gaining access to user accounts in cases where there is a saved logon.
What this means is that access to DNS records is security-critical. It should give any business pause for thought. How strong is the username/password which gives access to your ISP or registrar’s control panel, allowing the DNS records to be changed? How secure are the servers themselves at that ISP or registrar – it is this that was cracked in this case, according to Zone-h.
Fixing a DNS problem is never instant, since records are replicated across the internet and any changes take time to propagate. This also explains why some users see hacked sites, while others get through to the correct destination. It is possible that the hackers chose to strike at the weekend, in the hope that corrective action would take longer. At the time of writing (23.30 on Sunday) the sites I checked have been fixed at source, including The Register and The Daily Telegraph, but some users are still seeing defaced sites.
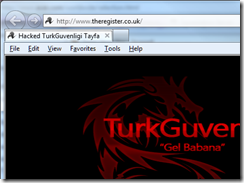
It’s frightening to think that such a vital part of the Internet infrastructure can be infiltrated using SQL injection techniques. After all, avoiding SQL injection is hardly rocket science these days – as I discussed at http://blog.mattmags.com/2006/05/31/writing-secure-code/.